Related Topics
 A PDF file for end-to-end Azure/Entra configuration for all Process Director features can be found here: Configuring Azure For Process Director (PDF Download)
A PDF file for end-to-end Azure/Entra configuration for all Process Director features can be found here: Configuring Azure For Process Director (PDF Download)
 This topic discusses a product feature in active development, and is subject to change at any time.
This topic discusses a product feature in active development, and is subject to change at any time.
There are several ways to register external applications for use in Azure; however, only Enterprise applications currently support SAML. Thus for this topic, we'll cover the creation of the Enterprise Application for configuring SAML with Process Director.
To begin creating the Enterprise application for SAML integration, first navigate to the Microsoft Entra ID page of your Azure portal.
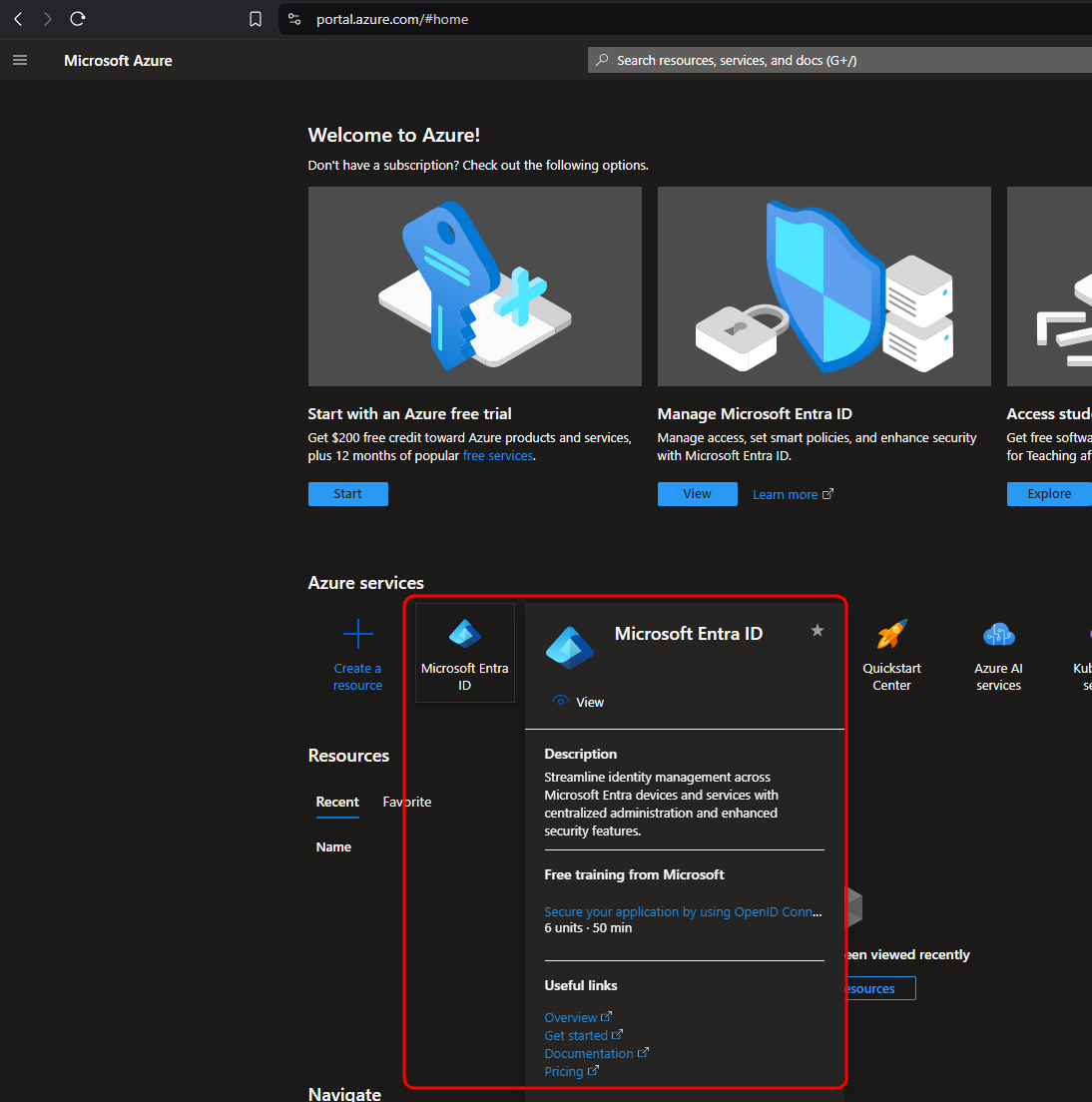
From this page, use the navigation bar on the left side of the screen to navigate to the Enterprise Applications page.
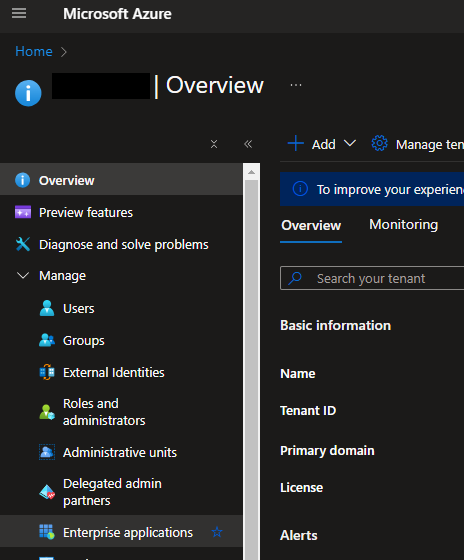
From the toolbar at the top of the page, select the New application button.
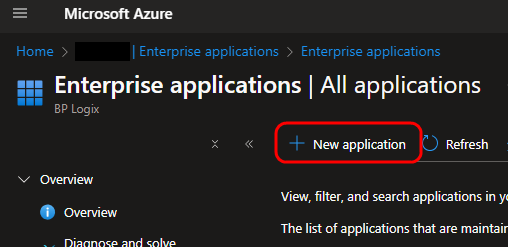
Click the Create your own application button, then select the option labeled, Integrate any other application you don't find in the gallery.
Once the application has been created, you'll need to select the application type. To do so, click the Single sign-on button from the navigation bar on the left side of the page, then click the SAML button that will appear in the main portion of the screen.
On the SAML-based Sign-on page, you'll need to add the appropriate identifying URLS to configure the linkage between Process Director's SAML-related pages and Azure/Entra.
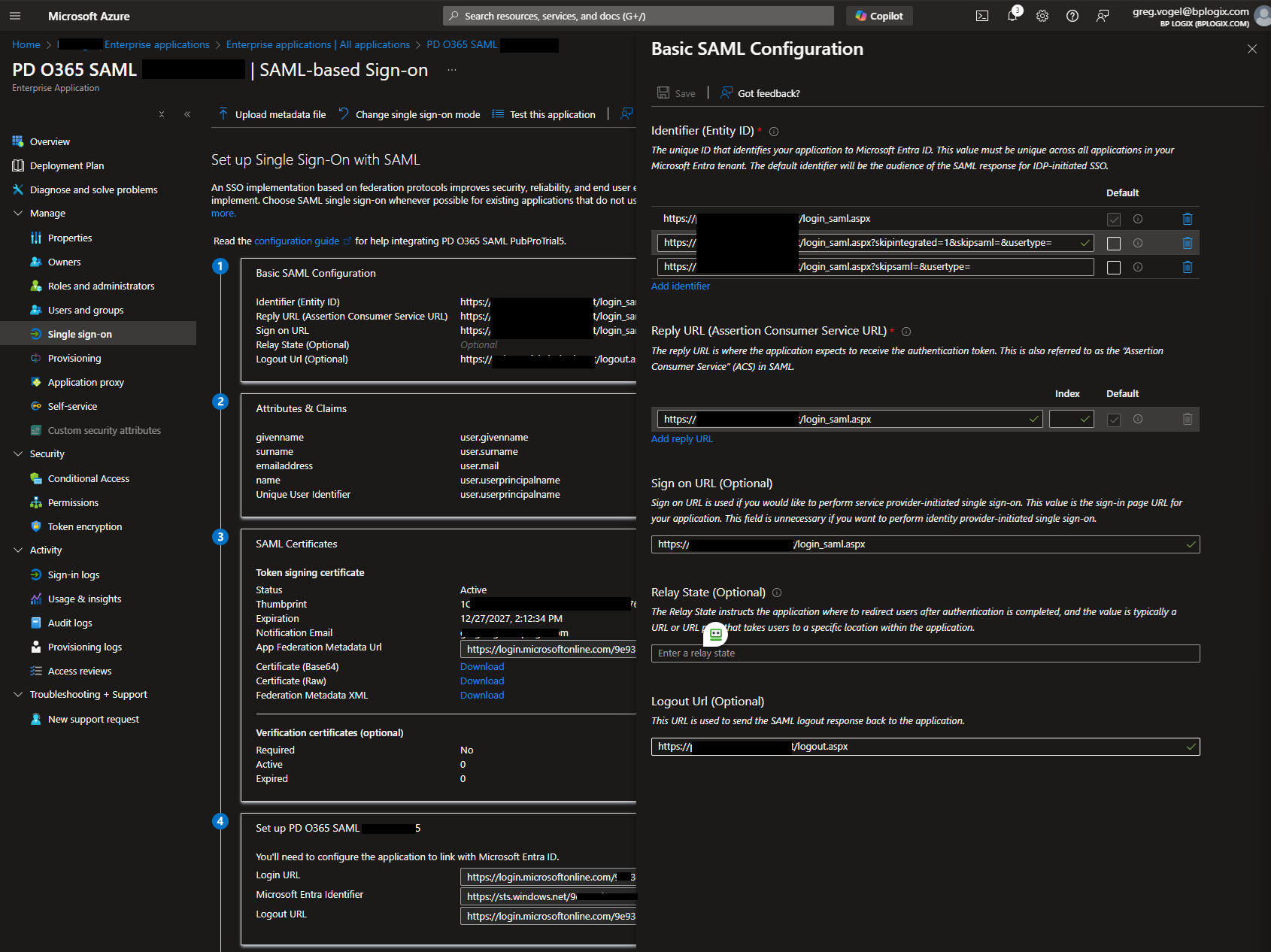
First, you'll need to add the Identifier (Identity ID) URLs that specify where the SAML logins will originate in Process Director. There are three of them that must be configured, using your actual Process Director server domain in place of the <pdserver.domain> placeholder text:
https://<pdserver.domain>/login_saml.aspxhttps://<pdserver.domain>/login_saml.aspx?skipintegrated=1&skipsaml=&usertype=https://<pdserver.domain>/login_saml.aspx?skipsaml=&usertype=
You'll then need to set the Reply URL (Assertion Consumer Service URL) property to:
https://<pdserver.domain>/login_saml.aspx.
Next, set the Signon URL (Optional) property to:
https://<pdserver.domain>/login_saml.aspx.
Finally, set the Logout Url (Optional) property to:
https://<pdserver.domain>/logout.aspx.
The remainder of the Azure default property settings can remain unchanged. Click the Save button to save your newly configured application. Keep the page open, however, as we'll want to test the configuration later.
With the application configured in Azure, you'll now need to make the appropriate changes to your Process Director installation to enable SAML sign on for Process Director. For Cloud customers, this process will most likely be done by BP Logix personnel. On-Premise customers, however, will have to perform this configuration in their Process Director installation. Please see the appropriate Process Director documentation for configuring SAML 2.0 (Federated Identity) Support in the Installation Guide. This configuration will require setting several SAML Custom Variables in your Custom Variables file.
Once SAML is correctly configured in Process Director, you can return to the Azure Application window. At the bottom of the configuration page, click the Test button. This button will verify that all your changes work by opening a pop-up browser window to perform the connection testing. It will even look up errors you may receive from Microsoft’s login server and provide you help with resolving them.
Once the testing is complete, and you've corrected any SAML configuration or connection errors that may appear, your Process Director server should be fully integrated with Azure for SAML authentication.
With the configuration completed, you'll then need to determine how existing users will be added to Process Director from your SAML system. There are two common methods for adding existing users:
- Direct import into Process Director via a CSV/Excel file.
- Enabling Process Director to auto-create user accounts when the user first logs in via SAML.
BP Logix personnel will work with you to determine the most appropriate method for your user provisioning, both initially and on an ongoing basis. There are, as always, pros and cons with both methods, so BP Logix will work with you to determine the user provisioning method that best meets your needs.
With SAML set up properly, you can move to the next step, which is to create and configure the "Full Scope" App Registration in Azure.
Other M365 CDA Configuration Topics
M365 CDA Configuration Process
- Create and configure “Full Scope” App Registration for PD in Azure/Entra.
- Create and configure “Site” App Registration for PD in Azure/Entra.
- Grant proper “Site” App Registration permission.
- Securely exchange “Site” App Registration and related settings with Process Director.
- Configure Process Director to leverage the application registration.
- Configure SharePoint external sharing.
Documentation Feedback and Questions
If you notice some way that this document can be improved, we're happy to hear your suggestions. Similarly, if you can't find an answer you're looking for, ask it via feedback. Simply click on the button below to provide us with your feedback or ask a question. Please remember, though, that not every issue can be addressed through documentation. So, if you have a specific technical issue with Process Director, please open a support ticket.

